Even if the iPhone is locked, i.e. not unlocked with a passcode, Touch ID or Face ID, you can still do various actions with it. This is useful if you find someone's phone or someone finds yours. You can communicate with the person in question. On the other hand, it also brings with it certain security risks, especially in a collective. If you wake up your iPhone but don't unlock it, you can see the flashlight icon or the Camera app on the main screen, in addition to the current time and date. In both cases, it is enough to hold your finger on the icon for a longer time, which will start the flashlight or redirect you to the camera. The one here has such a limitation that you cannot look at the last photos taken. You can't talk too much about the threat to privacy here, because no one has access to the essential functions of the iPhone in this way.
It could be interest you

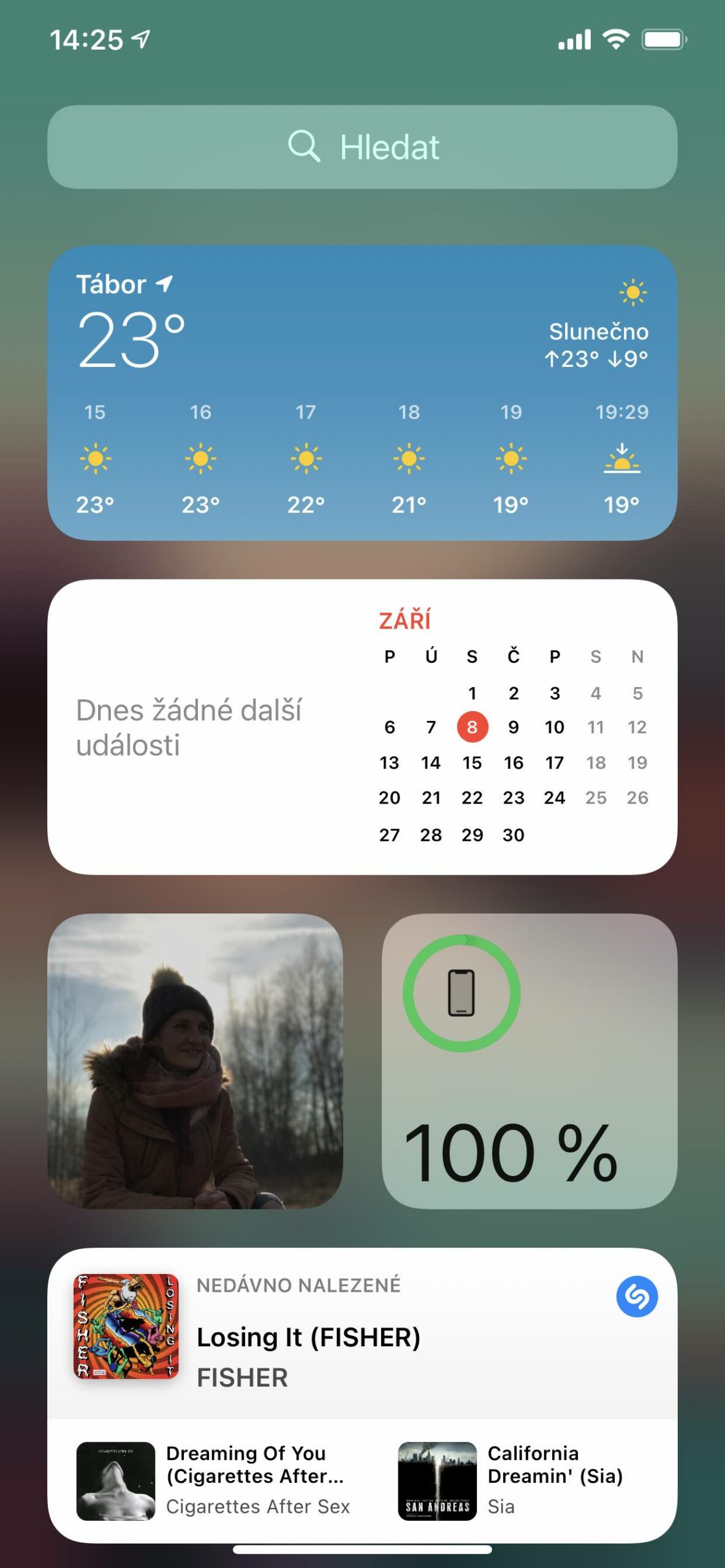
Displayed information on the iPhone display
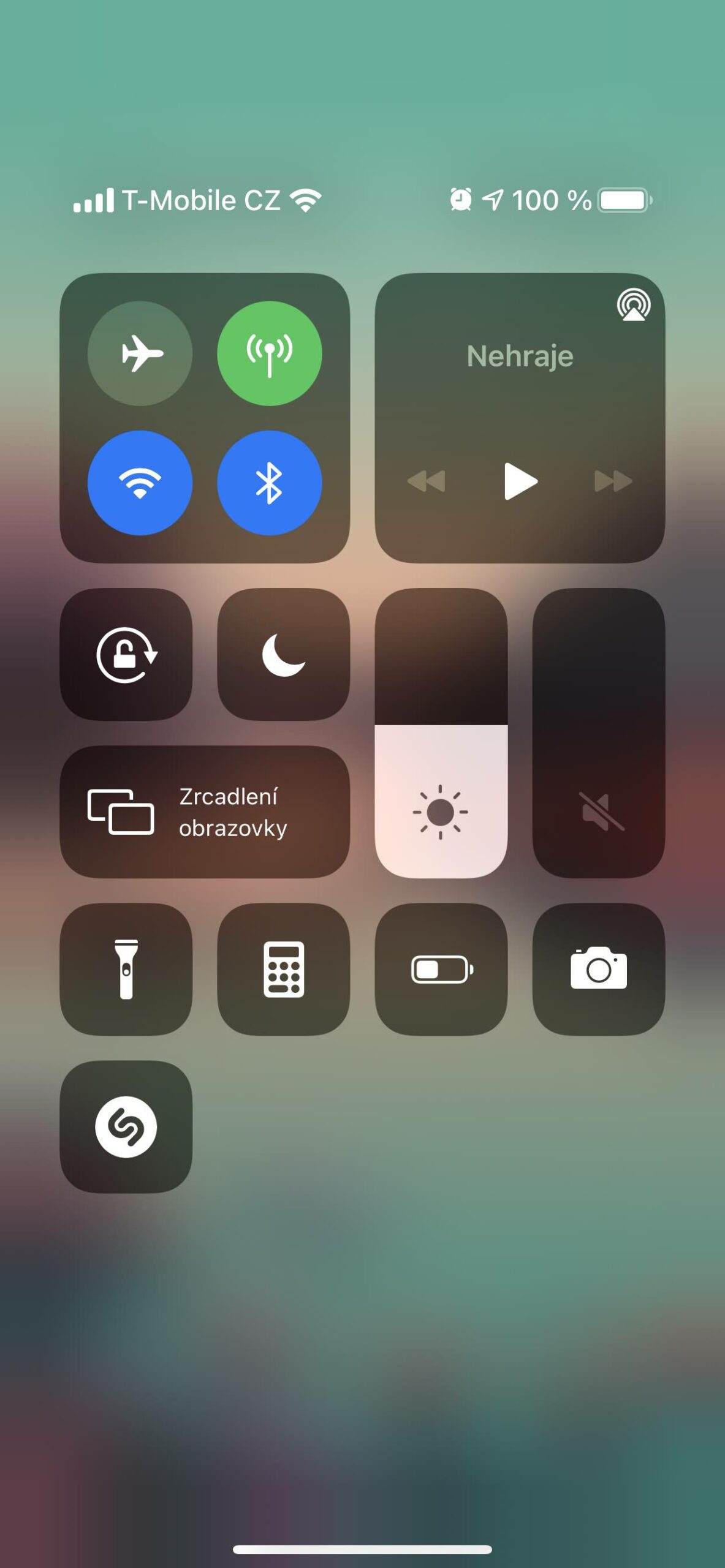
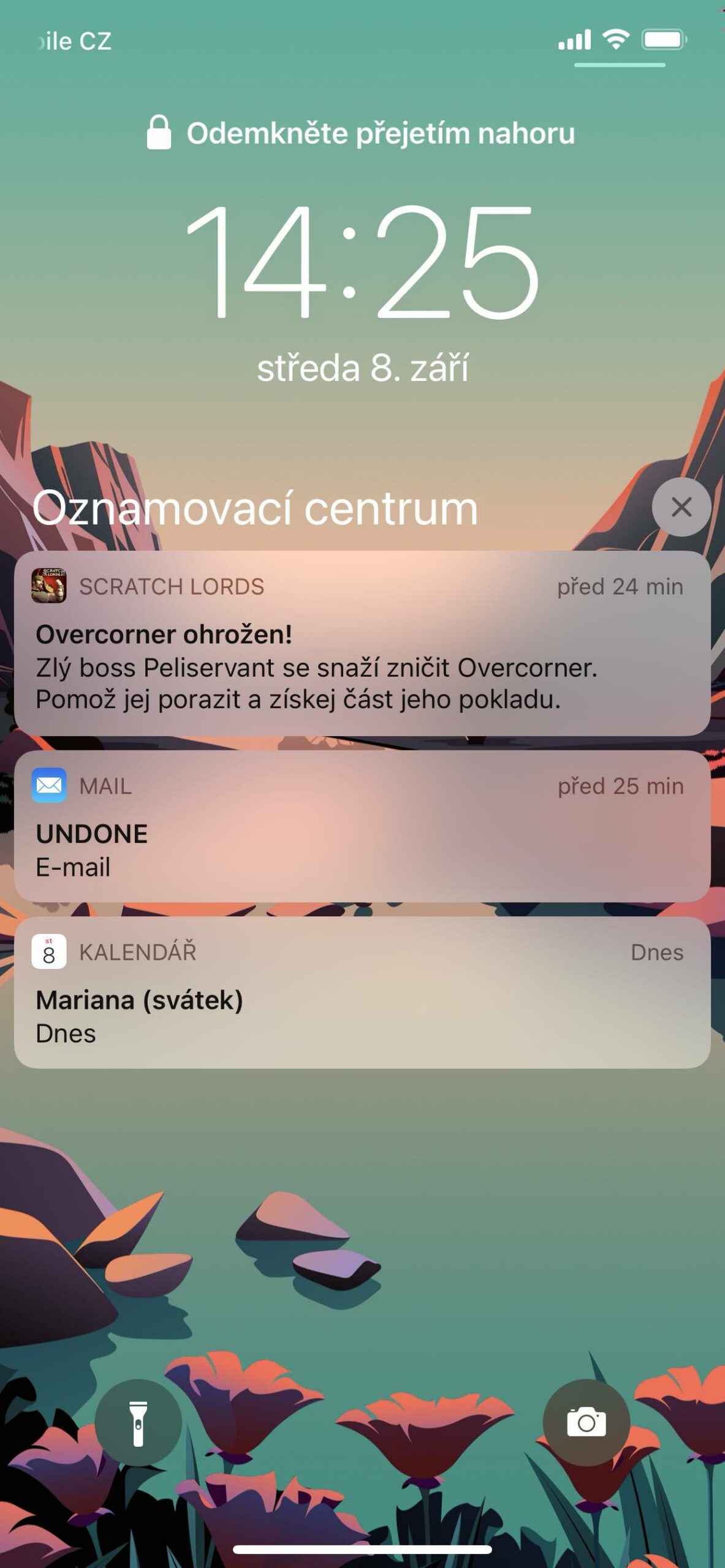
On the locked screen, however, you can also view notifications, if any, or go to the Control Center, for example. The former is critical in that you, or anyone else, can answer them. So if someone gets hold of your phone, they can abuse it. This is also true in the second case where it easily turns off mobile signal reception, Wi-Fi and Bluetooth etc.
And on top of that, there is also the option to read information from widgets, in which you can, for example, have scheduled meetings, access Siri, home control, Wallet, or call back the numbers of missed calls. But you can define all of this. The procedure is as follows:
- Go to Settings.
- Choose Face ID and code or Touch ID and code lock.
- Authorize yourself device code.
- Go all the way down to the section Allow access when locked.
You can then enable or disable options that you don't want to be accessible from the lock screen. If you change your device's default settings to allow, for example, a USB connection to a locked iPhone, be aware that this will disable important security protections. A potential attacker could thus connect the iPhone to the computer and get your sensitive data from it even without a code.
 Adam Kos
Adam Kos