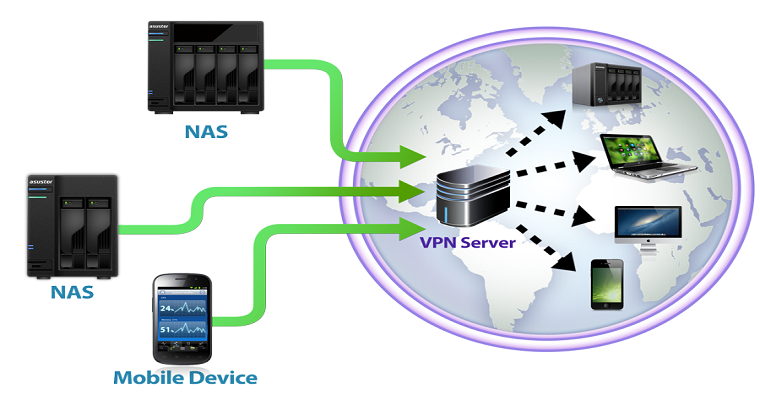
A serious vulnerability related to connecting to VPN networks appears in the operating system iOS 13.3.1 and later. This vulnerability prevents all network traffic from being encrypted. The bug was pointed out by ProtonVPN, which was also the first to discover it. The flaw in question allows bypassing VPN encryption, potentially compromising the security of user data, and also sharing the user's IP address.
It could be interest you

Not only in the iOS and iPadOS operating system, in the case of activating a VPN connection, all other network connections should be terminated and the connection restored in an encrypted form. However, due to a bug that first appeared in iOS 13.3.1 and has not yet been fixed, this procedure does not happen when connecting to a VPN. Instead of terminating all connections and restarting them encrypted, some connections remain open, allowing network connections to bypass VPN encryption. With such unsecured connections, data and the user's IP address may be revealed, and thus also their potential identification. According to ProtonVPN, users in countries where citizens are being monitored and their rights are being violated are also at risk due to this bug.
Only certain processes with short-lived connections "behave" in the vulnerable manner described above. One of them is, for example, the push notification system from Apple. Unfortunately, there is nothing VPN app and tool makers can do about the aforementioned error. Users have no choice but to manually end and re-enable all network connections. They do this by activating Airplane mode, which they deactivate again after connecting to a VPN. Activating Airplane mode will immediately and completely terminate all ongoing connections. It is then restored in an encrypted form after the VPN is activated. The described solution is currently the only way to deal with this error. Apple is reportedly aware of the vulnerability, so it's likely that users will see a fix in one of the next iOS updates.


And how do I connect to the VPN when the iPhone is in airplane mode and therefore not connected to the Internet?
I apologize for the question. I tried it now and it seems that even in airplane mode it connects to the VPN. I don't know how, but it seems to work.