The AirTag smart locator hasn't even been on the market for two weeks and it's already been hacked. This was taken care of by German security expert Thomas Roth, who goes by the nickname Stack Smashing, who was able to penetrate directly into the microcontroller and subsequently modify its firmware. The expert informed about everything through posts on Twitter. It was the intrusion into the microcontroller that allowed him to change the URL address to which the AirTag then refers in loss mode.
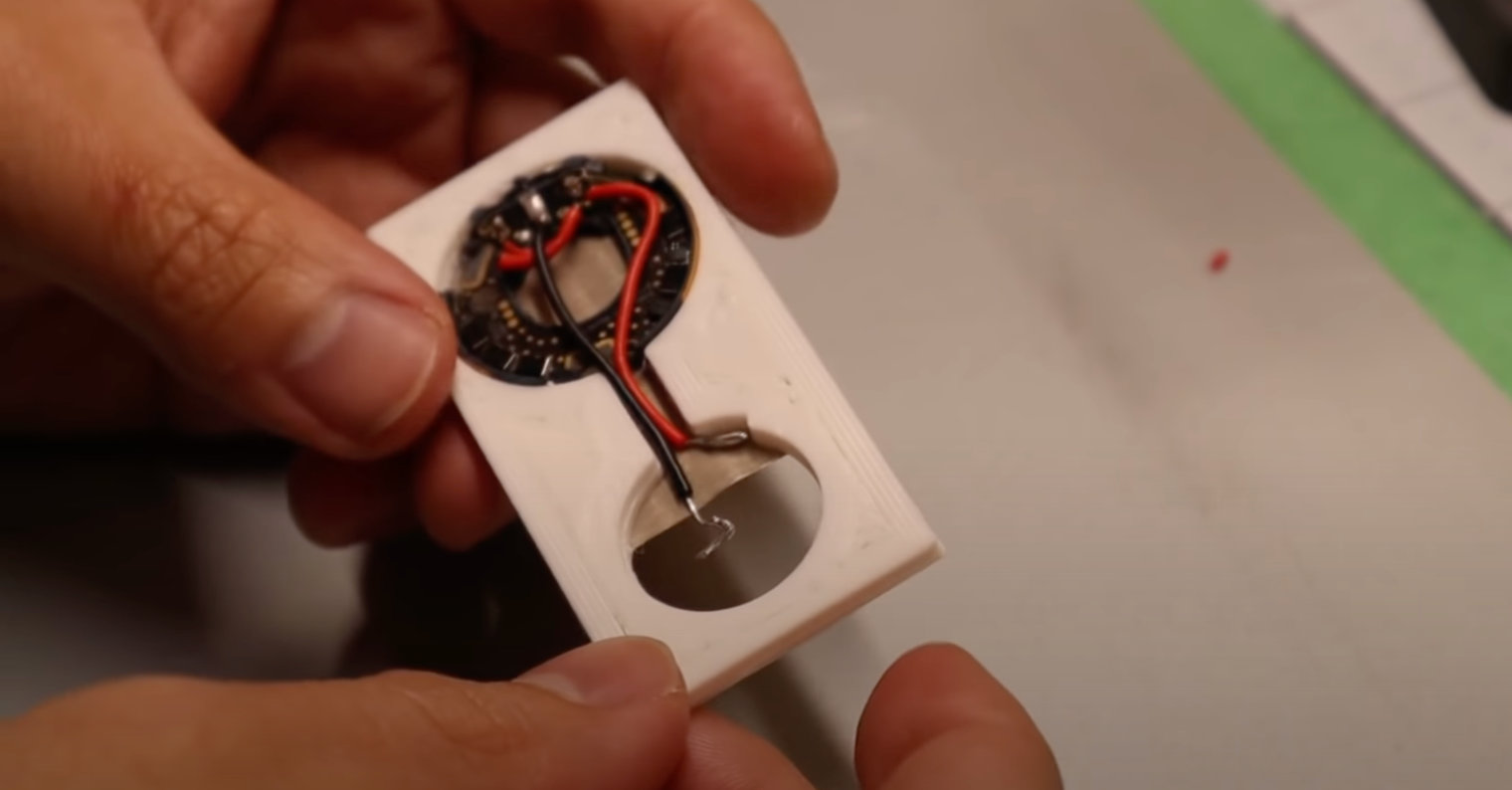
Yesss !!! After hours of trying (and bricking 2 AirTags) I managed to break into the microcontroller of the AirTag! 🥳🥳🥳
/ cc @colinoflynn @LennertWo pic.twitter.com/zGALc2S2Ph
- stacksmashing (@ghidraninja) May 8, 2021
In practice, it works so that when such a locator is in loss mode, someone finds it and puts it to their iPhone (for communication via NFC), the phone will offer them to open a website. This is how the product works normally, when it subsequently refers to information entered directly by the original owner. Anyway, this change allows hackers to choose any URL. The user who subsequently finds the AirTag can access any website. Roth also shared a short video on Twitter (see below) showing the difference between a normal and a hacked AirTag. At the same time, we must not forget to mention that breaking into the microcontroller is the biggest obstacle against manipulating the hardware of the device, which has now been done anyway.
Of course, this imperfection is easily exploited and can be dangerous in the wrong hands. Hackers could use this procedure, for example, for phishing, where they would lure sensitive data from victims. At the same time, it opens the door for other fans who can now start modifying the AirTag. How Apple will deal with this is unclear for now. The worst case scenario is that the locator modified in this way will still be fully functional and cannot be remotely blocked in the Find My network. The second option sounds better. According to her, the giant from Cupertino could treat this fact through a software update.
Built a quick demo: AirTag with modified NFC URL 😎
(Cables only used for power) pic.twitter.com/DrMIK49Tu0
- stacksmashing (@ghidraninja) May 8, 2021
It could be interest you











Just a sensation, an unnecessarily inflated bubble. This has no major impact on the AirTag's primary purpose. I don't think we have to worry about some mass hacking of our key fobs at all.
And what did he achieve? I don't see how it could be good for anyone.
Yep, that's Apple's famous security :-(
For me, AirTag is a completely useless device! There are many others on the market, with the same functions, and as a bonus for a third of the price :-)