On the website of Felix Kraus, the developer behind the program fast lane, a very interesting piece of information has emerged today regarding the latest method of conducting a phishing attack that is currently possible to perform on the iOS platform. This attack targets the device user's password and is dangerous mainly because it looks really real. And to such an extent that the attacked user could lose his password on his own initiative.
It could be interest you

Felix on his own site represents a new concept of a phishing attack that can get onto iOS devices. This is not happening yet (although it has been possible for several years), it is only a demonstration of what is possible. Logically, the author does not display the source code of this hack on his website, but it is not unlikely that someone will try it.
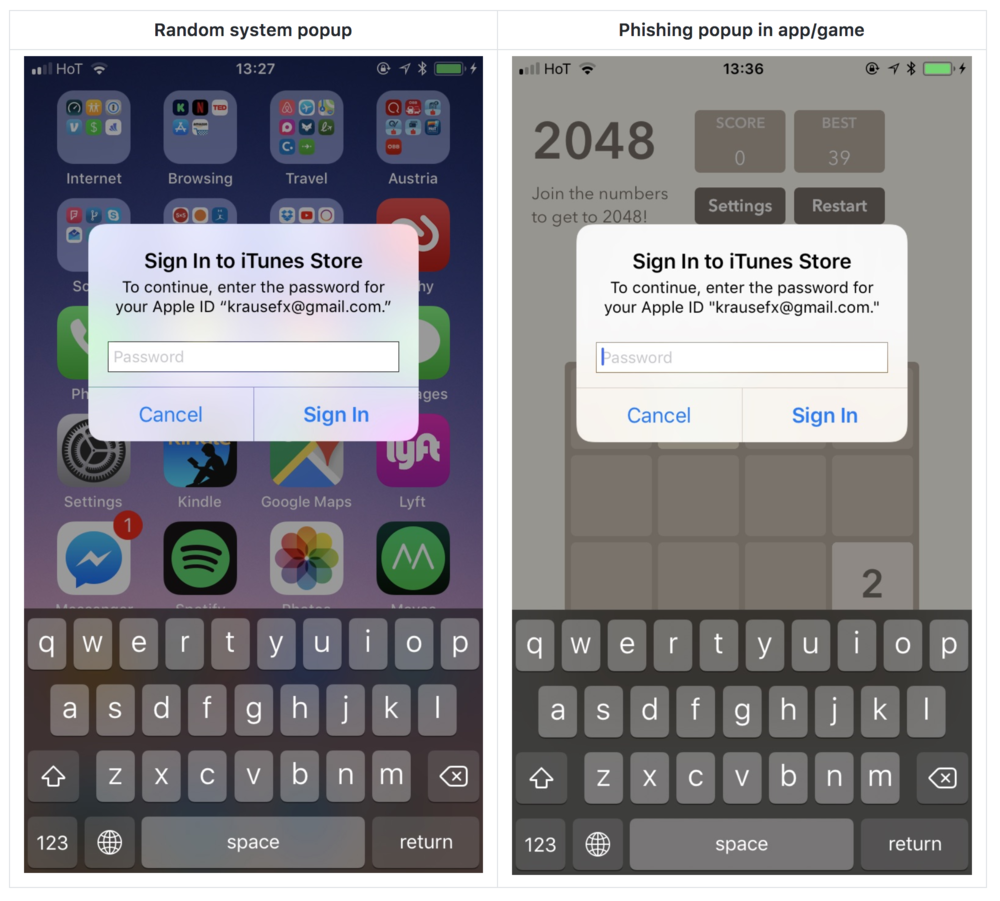
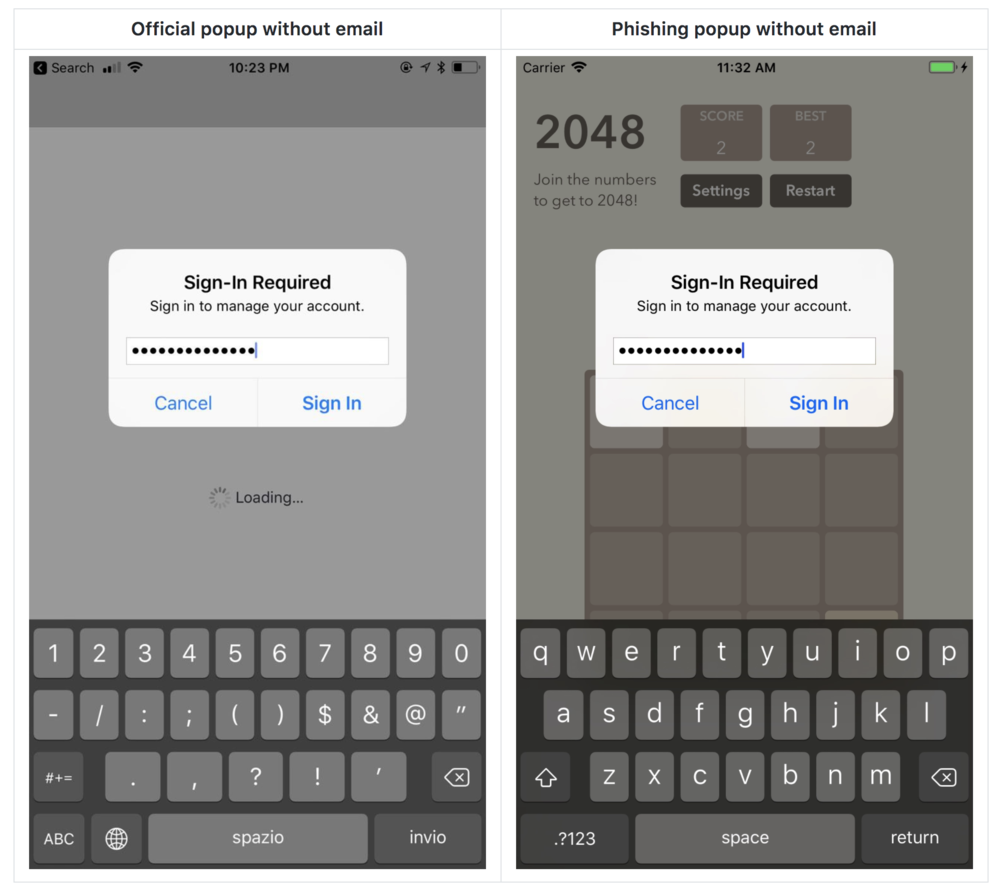
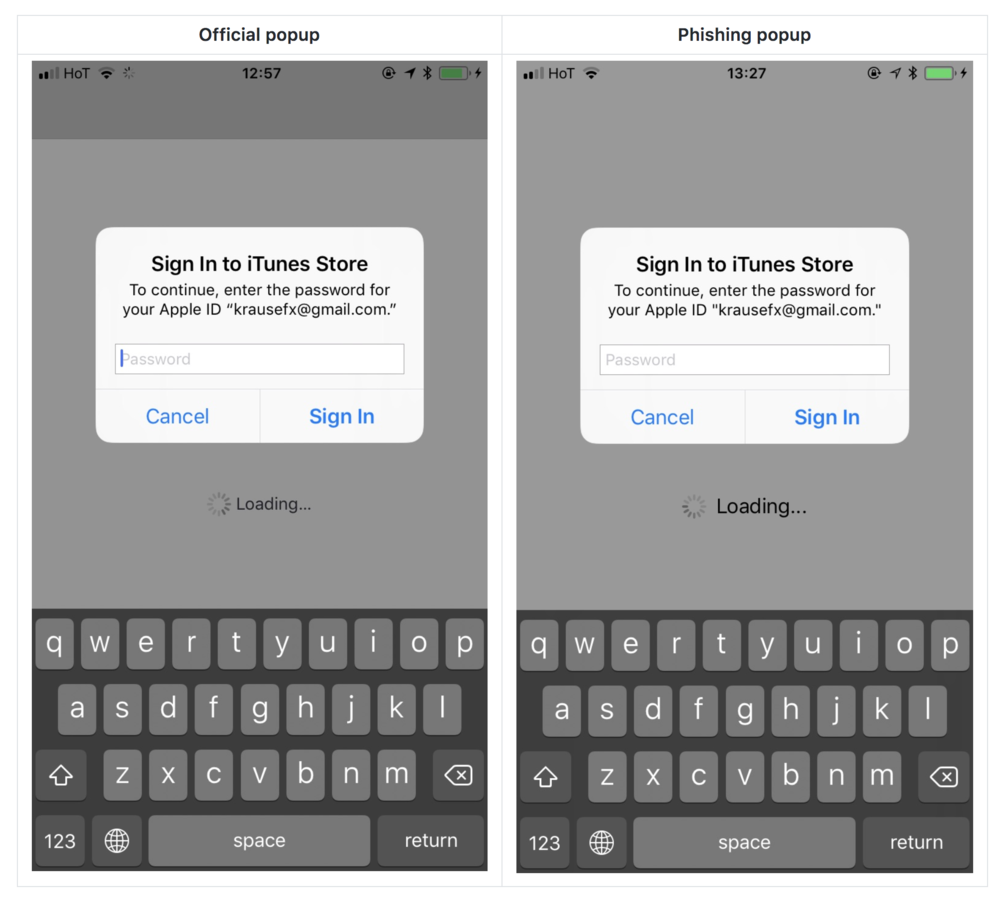
Basically, it's an attack that uses an iOS dialog box to get the user's Apple ID account password. The problem is that this window is indistinguishable from the real one that appears when you authorize actions on iCloud or the App Store.
It could be interest you

Users are used to this pop-up and basically fill it automatically when it appears. The problem arises when the originator of this window is not the system as such, but a malicious attack. You can see what this type of attack looks like in the images in the gallery. Felix's website describes exactly how such an attack can occur and how it can be exploited. It is enough that the installed application in the iOS device contains a specific script that initializes this user interface interaction.
Defense against this type of attack is relatively easy, but few would think to use it. If you ever get a window like this and you suspect something is not quite right, just press the Home Button (or its software equivalent…). The app will crash into the background, and if the password dialog was legitimate, you'll still see it on your screen. If it was a phishing attack, the window will disappear when the application is closed. You can find more methods at author's website, which I recommend reading. It's probably only a matter of time before similar attacks spread to apps in the App Store.
Source: krausefx
So such an attack in a legitimate application would probably not pass Apple control, right?
So again, if you don't have a jailbreak, you have nowhere to catch it.
PS: I have never seen this "regular" voice before. I use Touch ID everywhere ;-).
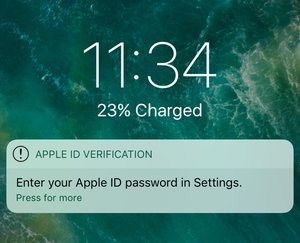
Well, I already saw her today. And there is no TID on the iPad mini. Just last night I got an email that someone was trying to sign in with my Apple ID from Chrome on Windows. Of course, I immediately changed the password in the morning. In the morning, when my SIM-free iPad mini got on wifi and the internet, it reported as lost and locked, and I got a message about it in my email. I assume that changing the password solved everything, but everyone should really be careful. I was most surprised by the message on the iPad's display, see picture. That doesn't seem quite standard to me, and the email address says it all - it's a scam and they wanted to get my login details.
… see picture. https://uploads.disquscdn.com/images/81787f49f7358d75acc8a8265cc5014288f07bed46bceeca1254da2086501947.png
And what kind of App was that, if I may ask?
Thank you.
I don't know about any app, I'm not aware of anything. I use the iPad little, practically almost single-purpose, and its equipment of applications corresponds to that - a few basic things, nothing else, empty. Apart from the occasional update (and there are few), I don't really install anything there, so this is the last of my devices where I would expect something like this.
And do you have Jailbreak?
Yeah sure, I'm dumb. They took your password and gave "lost device" and wrote a message. Pardon. The question is how they got your password. Do you have the same password for multiple services? It is leaked on the Internet (can be found on the website https://haveibeenpwned.com where do you enter your email or username)?
I'm just thinking that the boys didn't have it in mind when they left you the original password, although it's great for you, but that's what they call a clique.
Yeah, I guess it could have been. Of course he has a record on that site. But there must be every e-mail address older than 10 years. :-)
I don't have a jailbreak and never have.
There are also newer ones :-) All you had to do was have LinkedIn and Dropbox at the wrong time and it's already happening with you :-)
Heh, if I had written about this sometime after switching to 3GS, when I was thinking about it, I could have been "famous"... Nah, history doesn't play around :-D
On the other hand, if the window pops up at me and I am not aware that I would initiate an interaction with the AppStore, I give cancel without filling in the password...
This just happened to me while activating my iPhone. I hope it's enough to give a skip. I only fill in the password under my email.