What happens on your iPhone stays on your iPhone. This is exactly the slogan Apple boasted at the fair CES 2019 in Las Vegas. Although he did not directly participate in the fair, he had billboards paid for in Vegas that carried this very message. This is an allusion to the iconic message: "What happens in Vegas stays in Vegas.” On the occasion of CES 2019, companies presented themselves that do not place as much emphasis on user privacy and security as Apple.
It could be interest you

iPhones are protected on several levels. Their internal storage is encrypted, and no one can access the device without knowing the code or without going through biometric authentication. As such, the device is often also linked to a specific user's Apple ID through a so-called activation lock. Therefore, in the event of loss or theft, the other party has no chance of abusing the device. In general, it can therefore be stated that security is at a relatively high level. But the question is, can the same be said about the data we send to iCloud?
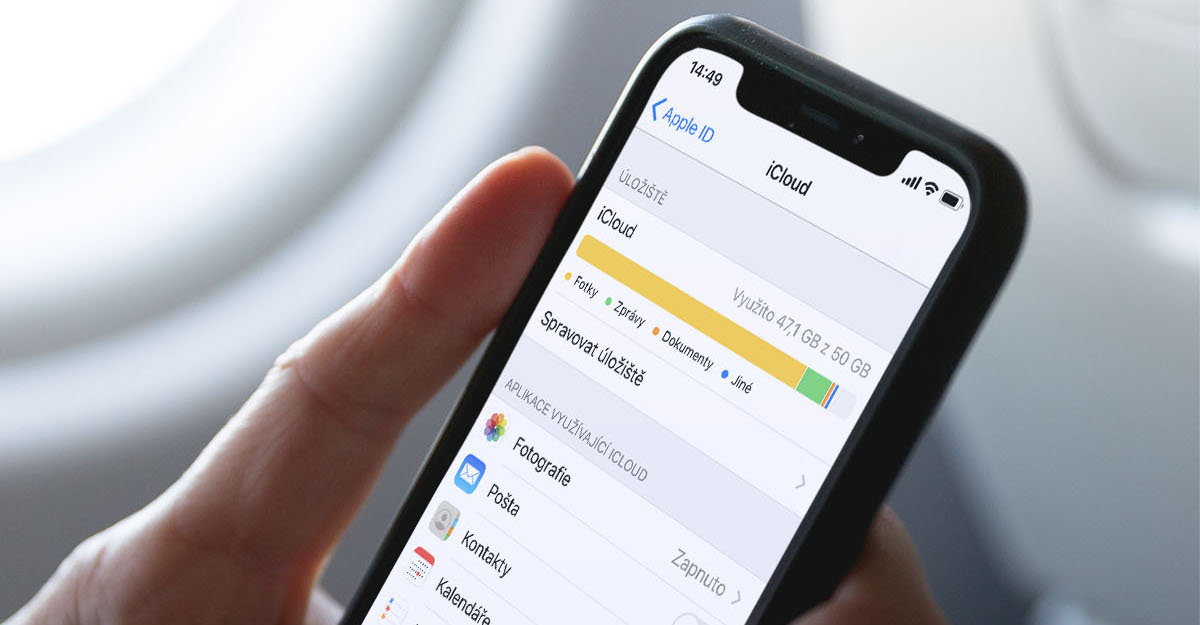
iCloud data encryption
It is generally known that the data on the device is more or less safe. We have also confirmed this above. But the problem arises when we send them to the Internet or to cloud storage. In that case, we no longer have such control over them, and as users we have to rely on others, namely Apple. In this case, the Cupertino giant uses two methods of encryption, which are quite fundamentally different from each other. So let's quickly run through the individual differences.
Data security
The first method Apple refers to as Data security. In this case, user data is encrypted in transit, on the server, or both. At first glance, it looks good - our information and data are encrypted, so there is no risk of their misuse. But unfortunately it's not that simple. Specifically, this means that although encryption is taking place, the necessary keys can also be accessed by Apple's software. Gigant states that the keys are only used for necessary processing. While this may be true, it raises various concerns about overall security. Although this is not a necessary risk, it is good to perceive this fact as a raised finger. In this way, for example, backups, calendars, contacts, iCloud Drive, notes, photos, reminders and many others are secured.

End-to-end encryption
The so-called is then offered as a second option End-to-end encryption. In practice, it is end-to-end encryption (sometimes also referred to as end-to-end), which already ensures real security and protection of user data. In this particular case, it works quite simply. The data is encrypted with a special key to which only you, as the user of a specific device, have access. But something like this requires active two-factor authentication and a set passcode. Very briefly, however, it can be said that the data that has this final encryption is really secure and no one else can simply get to it. In this way, Apple protects the key ring, data from the Household application, health data, payment data, history in Safari, screen time, passwords to Wi-Fi networks or even messages on iCloud in iCloud.
It could be interest you

(Un)secure messages
Simply put, "less important" data is protected in a labeled form Data security, while the more important ones already have end-to-end encryption. In such a case, however, we encounter a relatively fundamental problem, which can be an important obstacle for someone. We are talking about native messages and iMessage. Apple often likes to brag about the fact that they have the aforementioned end-to-end encryption. For iMessage specifically, this means that only you and the other party can access them. But the problem is that the messages are part of iCloud backups, which are not so lucky in terms of security. This is because backups rely on encryption in transit and on the server. So Apple can access them.

Messages are thus secured at a relatively high level. But once you have them backed up to your iCloud, this level of security theoretically drops. These differences in security are also the reason why some authorities sometimes get access to apple-growers' data and other times they don't. In the past, we could already record several stories when the FBI or CIA needed to unlock a criminal's device. Apple can't get directly into the iPhone, but it has access to (some) of the mentioned data on iCloud.
It could be interest you