From time to time, information appears on various forums or magazines that the security of an iPhone or other Apple device has been "broken". For example, it may be possible to broadcast all possible combinations of a code lock to a locked device, which are successively entered until the correct one is found. Such a procedure is usually performed by a special device that connects to the Lightning port. Sometimes there is also a procedure that can be used to get to an application via Siri, notifications or the control center, for example. Fortunately, there is a simple option in iOS to disable these features on the lock screen to prevent potential device abuse.
It could be interest you
How to defend against misuse of a locked iPhone
By default, you have access to the notification center on a locked iPhone, for example, you can also display notifications, activate Siri, or quickly answer a missed call. It is these options that may contain some kind of error that can be used to get into the device in some way. However, you can deny access to individual functions when locked:
- First, you need to move to the native application Settings.
- Once you've done that, go down a notch below, where locate and click the box Face ID (Touch ID) and code.
- On the next screen it is then necessary for you to use the code lock authorized.
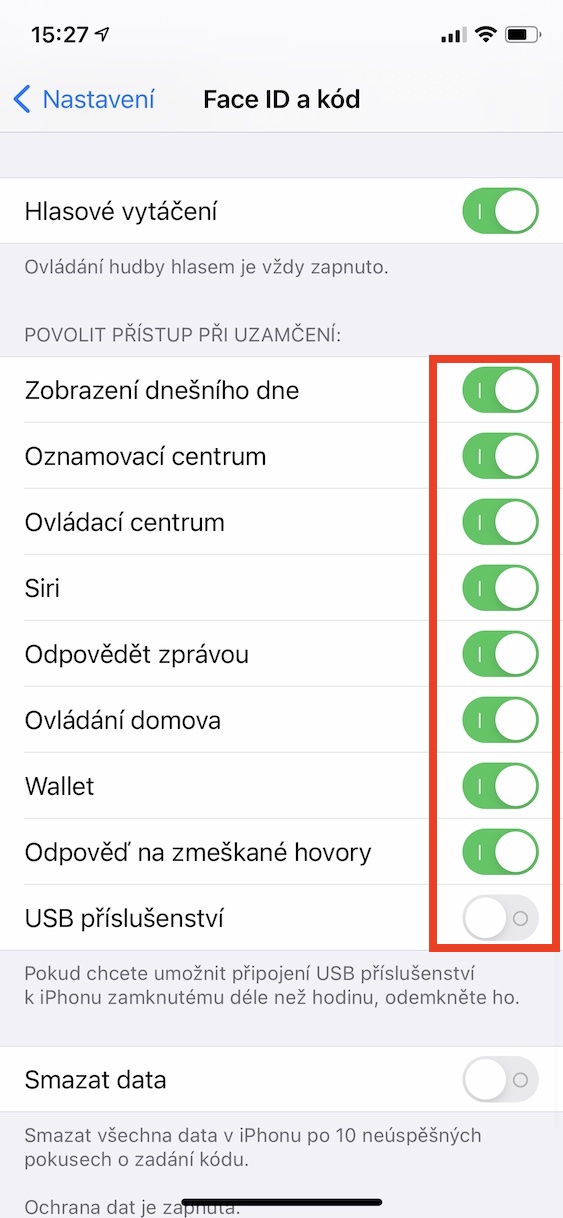
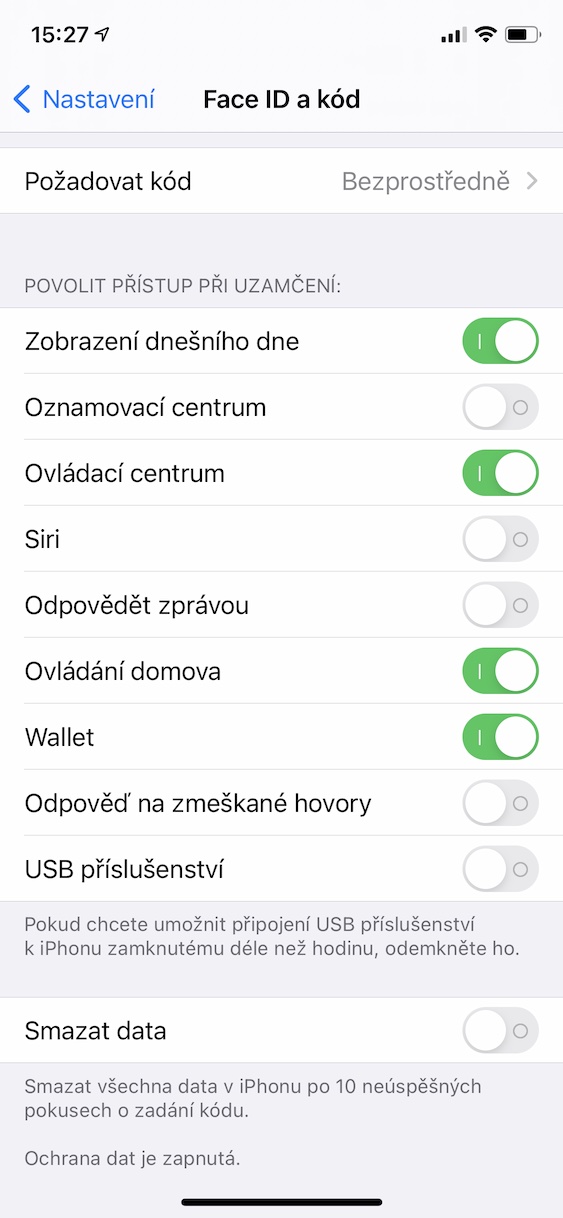
- Now scroll down again in this settings section below, up to the category Allow access when locked.
- It is already here individual functions, which you can access from the lock screen.
- Now all you have to do is help switches disabled access to individual functions on the locked screen.
Thus, in the above-mentioned way, you can achieve that it will not be possible to access certain functions on the locked screen of the iPhone, therefore you will avoid possible abuse. I personally recommend that you in the above section deactivated on the locked screen access at least for Notification center, Siri, Reply with message, Answer missed calls and USB accessories. Of course, if you want to be 10% protected, it is useful to deactivate all these options. In addition, you can then activate the Delete data option below, which guarantees that after XNUMX unsuccessful attempts to enter the code, all data will be deleted from the device.
 Flying around the world with Apple
Flying around the world with Apple