On Monday, we informed you about the first AirTag hack, which was taken care of by a German security expert. Specifically, he managed to break into the microcontroller and overwrite the firmware, thanks to which he was able to set an arbitrary URL that is then displayed to the finder when the product is in Lost mode. Another interesting thing flew across the internet today. Another security expert, Fabian Bräunlein, came up with a way to exploit the Find network to send messages.
It could be interest you

What is the Find Network
Let's first briefly recall what the Najít network actually is. It is a grouping of all Apple products that can communicate with each other and securely. This is what Apple uses primarily for its AirTag locator. It shares a relatively detailed location with its owner even when they move away from each other for several kilometers. It is enough for someone with an iPhone to pass by, for example, a lost AirTag. The two devices are connected immediately, the iPhone then sends information about the location of the locator in a secure form, and the owner can thus roughly see where he might be.
Network abuse Find
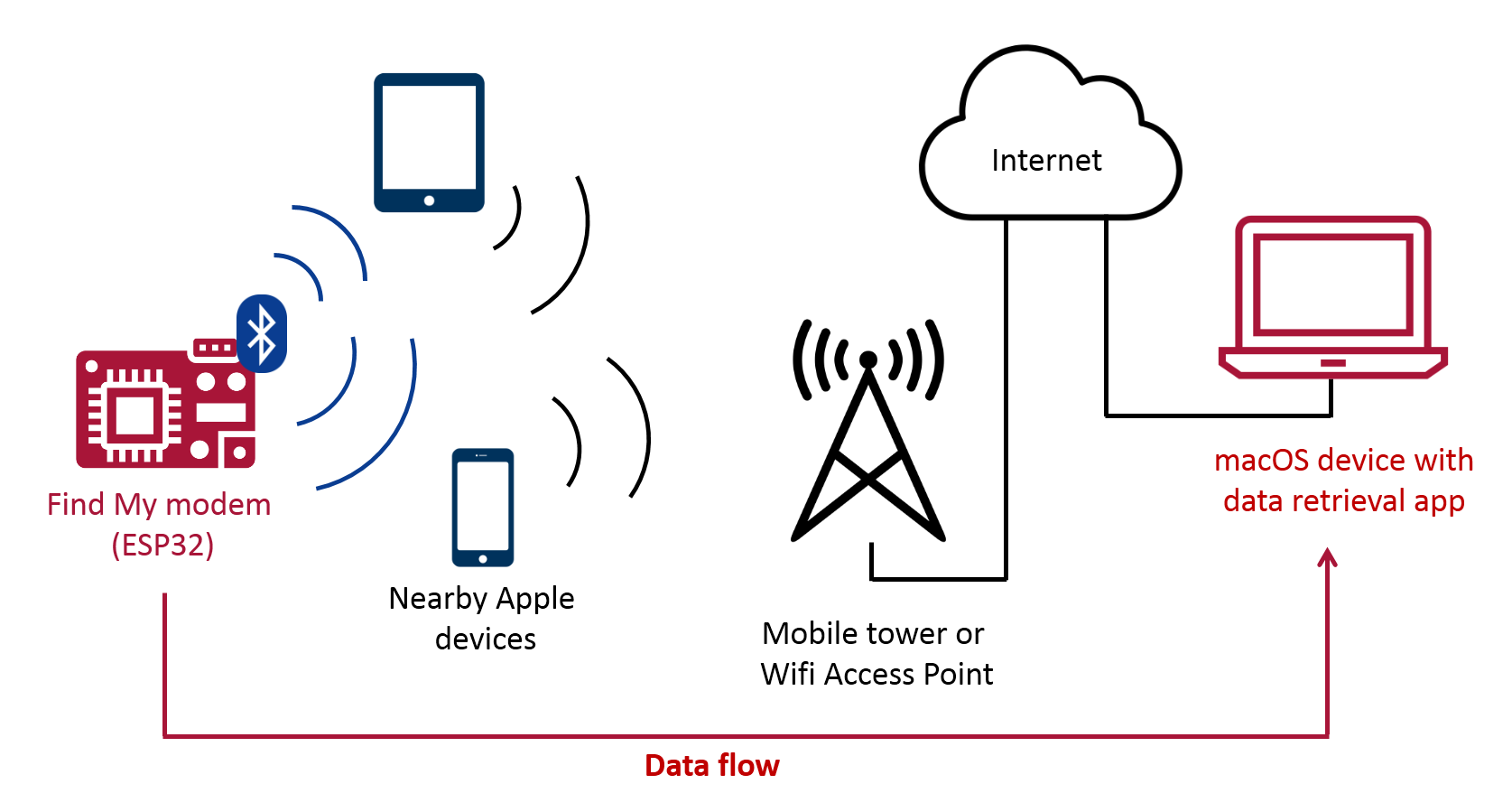
The aforementioned security expert had one thing in mind. If it is possible to send location information across the network in this way, even without an Internet connection (AirTag cannot connect to the Internet - editor's note), perhaps this could also be used for sending shorter messages. Bräunlein was able to exploit exactly that. In his demonstration, he also showed how large a text can actually be sent from the microcontroller itself, which runs its own version of the firmware. This text was subsequently received on a pre-prepared Mac, which was also equipped with its own application for decoding and displaying the received data.
For now, it is not entirely clear whether this procedure could become dangerous in the wrong hands, or how it could be misused. In any case, there are opinions on the Internet that Apple will not be able to prevent something like this so easily, paradoxically due to its great emphasis on privacy and the presence of end-to-end encryption. The expert described the whole process in detail in his own way blog.
It could be interest you









 Adam Kos
Adam Kos